Hacking/WebHacking Wargame Writeup
[WriteUp] / [webhacking.kr] old-5
Cooku222
2025. 6. 10. 15:22
-> 소스코드를 확인해본다.
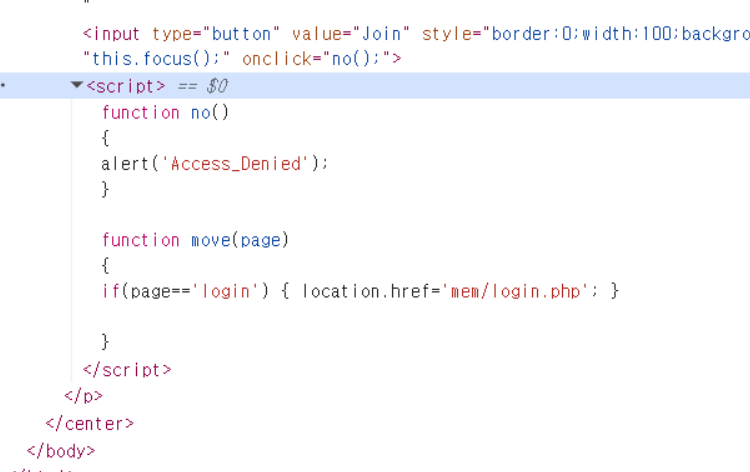

해당 페이지의 소스코드가 난잡하다
l='a';
ll='b';
lll='c';
llll='d';
lllll='e';
llllll='f';
lllllll='g';
llllllll='h';
lllllllll='i';
llllllllll='j';
lllllllllll='k';
llllllllllll='l';
lllllllllllll='m';
llllllllllllll='n';
lllllllllllllll='o';
llllllllllllllll='p';
lllllllllllllllll='q';
llllllllllllllllll='r';
lllllllllllllllllll='s';
llllllllllllllllllll='t';
lllllllllllllllllllll='u';
llllllllllllllllllllll='v';
lllllllllllllllllllllll='w';
llllllllllllllllllllllll='x';
lllllllllllllllllllllllll='y';
llllllllllllllllllllllllll='z';
I='1';
II='2';
III='3';
IIII='4';
IIIII='5';
IIIIII='6';
IIIIIII='7';
IIIIIIII='8';
IIIIIIIII='9';
IIIIIIIIII='0';
li='.';
ii='<';
iii='>';
lIllIllIllIllIllIllIllIllIllIl=lllllllllllllll+llllllllllll+llll+llllllllllllllllllllllllll+lllllllllllllll+lllllllllllll+ll+lllllllll+lllll;
lIIIIIIIIIIIIIIIIIIl=llll+lllllllllllllll+lll+lllllllllllllllllllll+lllllllllllll+lllll+llllllllllllll+llllllllllllllllllll+li+lll+lllllllllllllll+lllllllllllllll+lllllllllll+lllllllll+lllll;
if(eval(lIIIIIIIIIIIIIIIIIIl).indexOf(lIllIllIllIllIllIllIllIllIllIl)==-1)
{alert('bye');throw "stop";}if(eval(llll+lllllllllllllll+lll+lllllllllllllllllllll+lllllllllllll+lllll+llllllllllllll+llllllllllllllllllll+li+'U'+'R'+'L').indexOf(lllllllllllll+lllllllllllllll+llll+lllll+'='+I)==-1)
{alert('access_denied');
throw "stop";}
else{document.write('<font size=2 color=white>Join</font><p>');
document.write('.<p>.<p>.<p>.<p>.<p>');
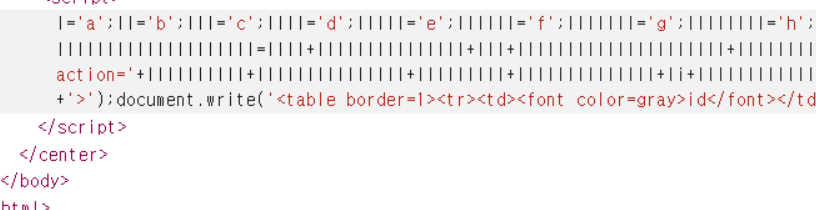
document.write('<form method=post action='+llllllllll+lllllllllllllll+lllllllll+llllllllllllll+li+llllllllllllllll+llllllll+llllllllllllllll+'>');
document.write('<table border=1><tr><td><font color=gray>id</font></td><td><input type=text name='+lllllllll+llll+' maxlength=20></td></tr>');
document.write('<tr><td><font color=gray>pass</font></td><td><input type=text name='+llllllllllllllll+lllllllllllllllllllllll+'></td></tr>');
document.write('<tr align=center><td colspan=2><input type=submit></td></tr></form></table>');}eval('document.cookie').indexOf('oldzombie') 는 실제로 document.cookie.indexOf('oldzombie')의 효과를 발휘함(타 롸업) 참고
-> WAF(Web Application Firewall)나 필터링 시스템이 document.cookie 직접 호출을 막을 경우에 쓰이는 방법이란다.. 알아두자.
-> 그리고 난독화 코드에 cookie 값에 oldzombie 라는 문자열이 존재하고 URL에 mode = 1이라는 문자열이 존재해야한다는 조건이 붙는다. -> oldzombie라는 쿠키 값을 생성 후 url에 mode = 1을 붙여준다.
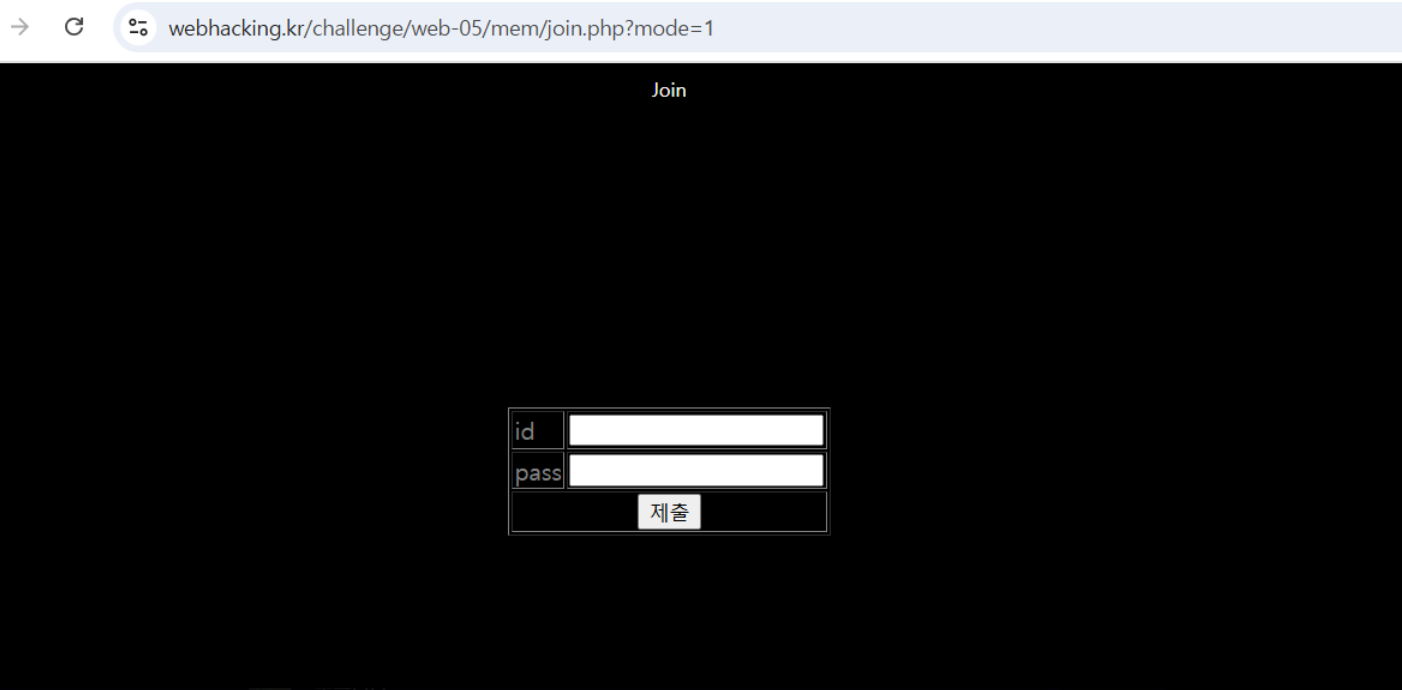
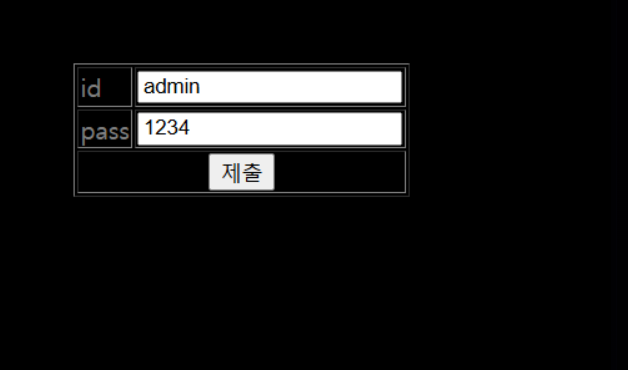
-> 목표로 한 join 사이트가 뜬다.
-> admin 계정으로 가입 시도하니까 아이디가 이미 존재한다고 뜸.


admin 양 옆에 공백 추가함
-> 그냥 admin과 공백이 앞에 존재하는 admin은 SQL에서 다른 값으로 카운트가 되기 때문에 우회가 될 거라고 예상함.
-> 우회 성공